Demystify Budget Priorities Crucial For A Resilient Cybersecurity Strategy | Forrester
Cyber Security
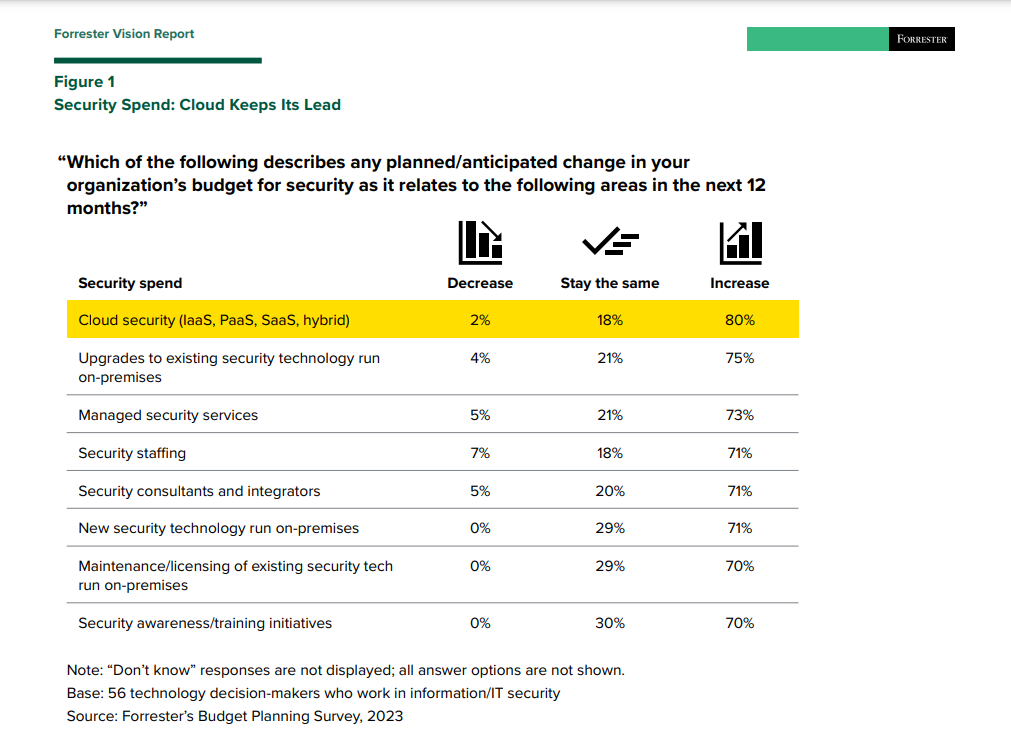
Investment Strategies for API Security, Detection, Zero Trust, and Cloud
Security leaders are advised to maintain or bolster investments in pivotal security controls and solutions safeguarding customer-facing operations, revenue-generating activities, and application programming interfaces (APIs).
Additionally, defending investments supportive of cloud migration endeavors and the transition to zero-trust architectures is paramount. Key recommendations for heightened investment or defense include:
- API Security: Prioritize protection measures for emerging business models and engagement platforms, addressing deficiencies in API security through a combination of traditional and developer-centric tools, alongside specialized solutions. Collaborate closely with development teams to reinforce API governance and ownership protocols.
- Phishing-Resistant MFA: Enhance security measures with multifactor authentication (MFA) solutions resistant to phishing attacks, leveraging technologies like FIDO keys and certificate-based authentication to fortify high-value targets against cyber threats.
- Third-Party Breach Control: Invest in dedicated platforms for robust third-party risk management (TPRM), ensuring comprehensive oversight of all external relationships, recurrent reassessment cycles, and risk threshold alignment with organizational objectives.
- Extended Detection and Response (XDR): Implement XDR technologies to streamline detection and response efforts, optimizing security team efficiency in identifying and mitigating evolving threats across diverse IT environments.
- Software Supply Chain Security: Strengthen product development and delivery processes by scrutinizing software components, pipeline tools, and development environments, utilizing software bill of materials (SBOM) and software composition analysis (SCA) tools to monitor security vulnerabilities continually.
- Zero Trust Network Access (ZTNA): Deploy ZTNA solutions to facilitate secure remote access, offering flexible policy-based controls for accessing resources across on-premises and cloud-based environments.
- Security Posture Management (SPM): Monitor and manage security configurations and data access within cloud infrastructure and SaaS applications, leveraging CSPM, CIEM, and SSPM solutions to ensure compliance and proactively mitigate cyber threats.
Divest Standalone On-Premises Security Tech And Redundant Solutions
Amidst evolving technological landscapes, it is prudent to divest from standalone on-premises security tools and redundant solutions to optimize resource allocation. Recommendations for decreased or avoided investments include:
- On-Premises Security Appliances: Reassess deployments of on-premises security appliances like secure web gateways (SWG), intrusion prevention systems (IPS), and data loss prevention (DLP), favoring cloud-based alternatives and integrated solutions for enhanced protection and operational efficiency.
- Low-Value Consulting Engagements: Streamline one-time or project-based consulting engagements, eliminating redundant assessments and audit preparations to mitigate engagement overload and optimize resource utilization.
- Standalone GRC Tools: Rationalize investments in standalone governance, risk, and compliance (GRC) tools, retiring legacy solutions and consolidating capabilities to enhance data integration and reporting efficiency.
- Endpoint Security Solutions: Transition from on-premises endpoint security solutions to cloud-delivered alternatives, leveraging the agility and scalability of cloud-native platforms to safeguard enterprise workloads effectively.
- Runtime Application Self-Protection (RASP): Redirect budgetary allocations from RASP towards solutions addressing modern application security challenges, such as API and container security, to align with evolving threat landscapes and technological advancements.
The Table of Contents of “Planning Guide 2024: Security And Risk”:
- Summary
- Constrained Economic Conditions And Emerging Risks Demand hyper-focus
- Cloud Security And Managed Services Spend Is Up, Other Areas Are Flat
- Invest Or Defend Investments In API Security, Detection, Zero Trust, And Cloud
- Divest Standalone On-Premises Security Tech And Redundant Solutions
- Experiment With CAASM, AI/ML Security, Distributed Identity, And ZT Edge
Number of Pages:
- 11 pages
Pricing:
- Free






